A “Zero Day” vulnerability is when a computer weakness is publicized and known bad actors are already exploiting it to take over computers.
A critical one for the Chrome Browser was published on 31 October 2019.
- Multiple Vulnerabilities in Google Chrome Could Allow for Arbitrary Code Execution (article published 31 October 2019)
- New Google Chrome Security Alert: Update Your Browsers As ‘High Severity’ Zero-Day Exploit Confirmed (article published 1 November 2019)
Our customers were able to concentrate on Halloween activities with their families and not worry about making sure everyone in the company went to their Google Chrome browser and initiated an update. The Chrome update was automatically pushed to all managed desktops that evening before the exploit was widely publicized.
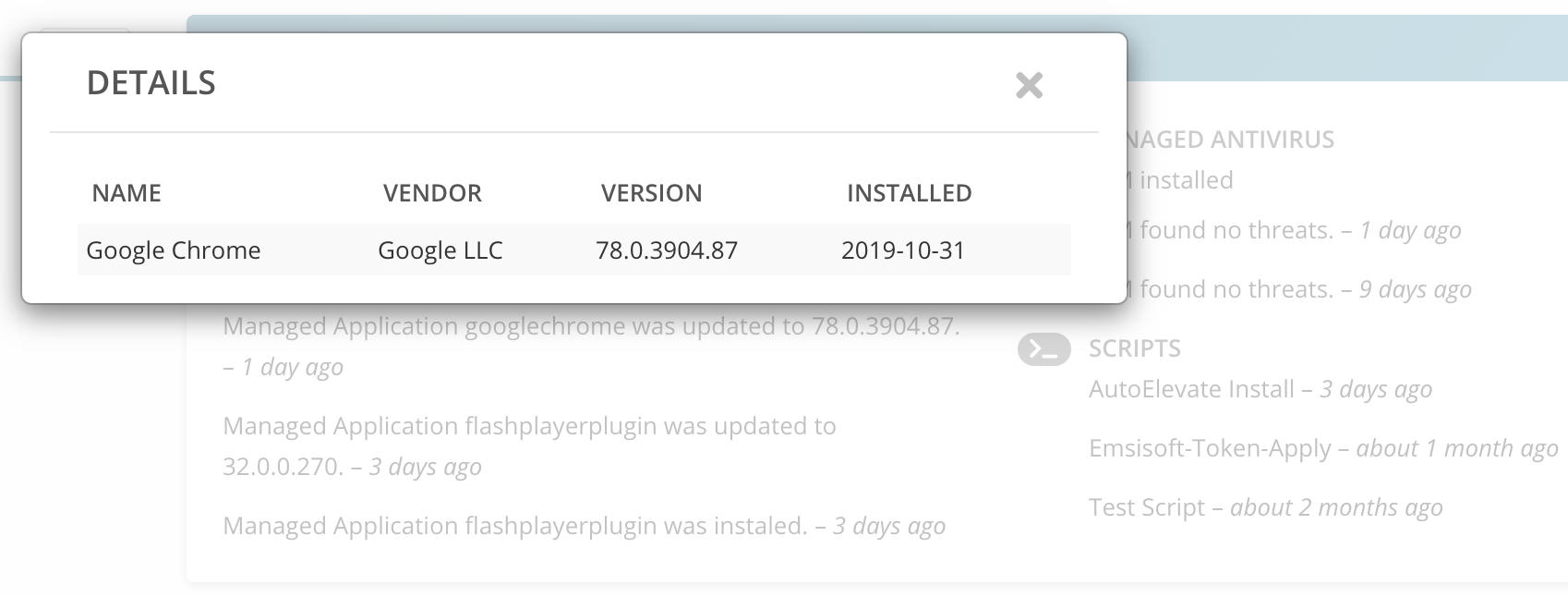
A good question is, since this is a zero day exploit, theoretically it could have already exposed a company’s computers to the exploit. This is true, and why a multi-layered approach to security is vital for protecting your company. No solution is 100% effective, but multiple layers help increase the odds greatly that if one layer fails, another layer will catch it.
In this case, our managed anti-virus solution would have scanned and possibly caught whatever code was attempted to be executed. But since this is so new, it’s possible that anti-virus would not catch it. Therefore our automated elevation protection would have forced any code trying to elevate privileges from executing until it could be manually reviewed and approved. Finally if that failed (due to it not requesting elevation) our breach detection service would look at the added code to see if it is a danger.
